Describe What a Service Is Traditionally Used for in Linux
It is the init system that manages the boot process once the initial booting is handed over from the bootloader ie GRUB or GRand Unified Bootloader. What is represented by the second number in the Linux kernel version 234.
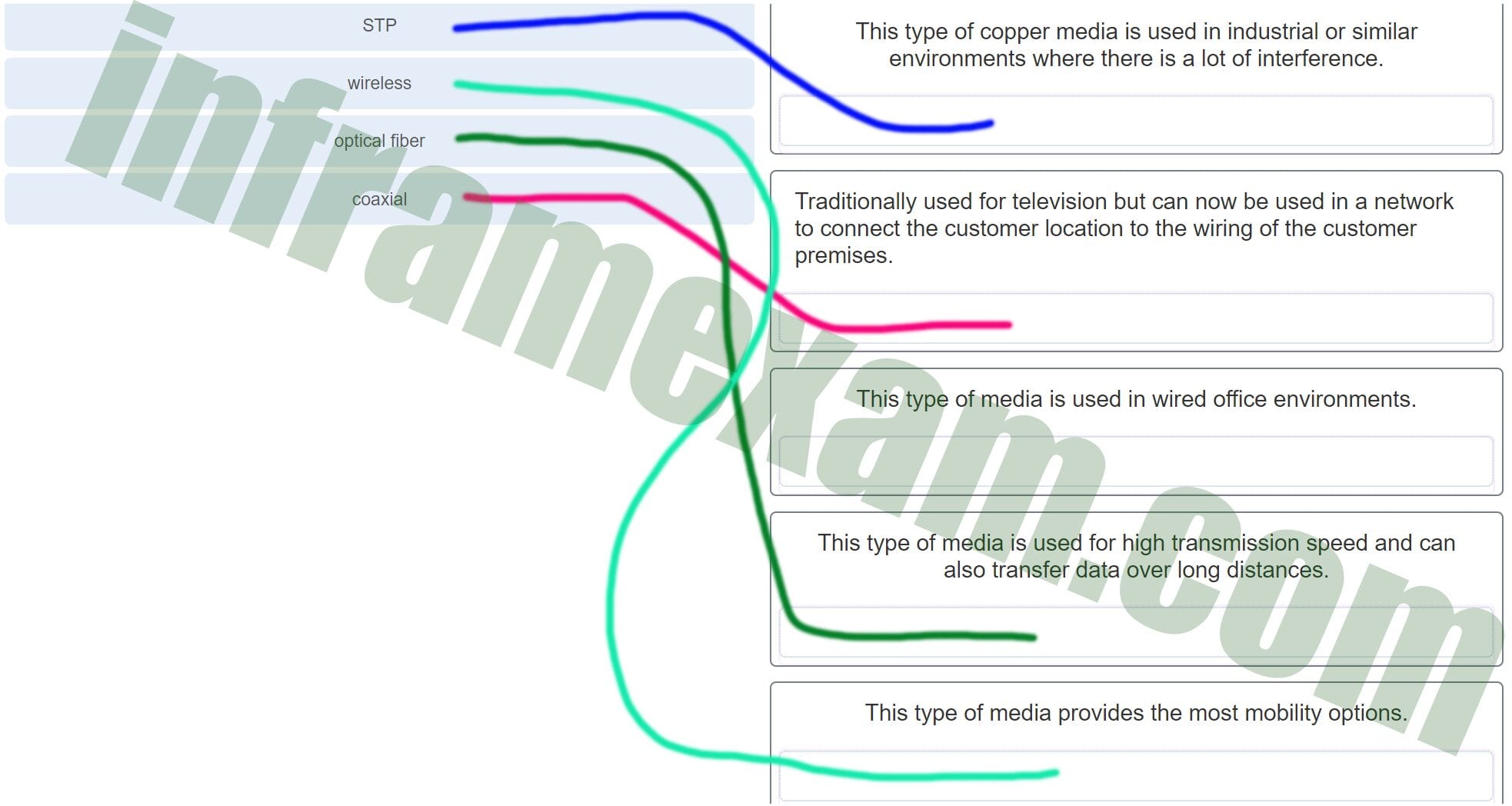
Match The Description With The Media Not All Options Are Used Premium It Exam Answers
It is a security measure to reduce the impact in case of an incident with one service compartmentalization and it simplifies administration as it becomes easier to track down what resources belong to which service.
. In server system a directory service such as LDAP and ADS is used for user management and authentication. The normal practice is to keep the software code in opt and then link the binary file in. What is The Linux Operating System Its Features.
Traditionally the opt directory is used for installingstoring the files of third-party applications that are not available from the distributions repository. Its full name is Unix Software Resource. Free and Open Source.
The file contains the service name port number and the protocol it uses as well as any aliases. The word hacker has traditionally defined someone who merely administers programs and generally enjoys computers. Systemd the main purpose of this daemon is to unify service configuration and behavior across Linux distributions.
This information is summarized in Table 2-2. Which e-mail service is responsible for sending messages between services. In this model the local system sends the users login information to the server system.
Up to 5 cash back Alternatively you can use the Berkeley Internet Name Domain service BIND for resolving hostnames to IP addresses. Its the traditional mountpoint for regular hard drive partitions file systems. Configuring BIND can be a real chore but once youve done it you can easily make changes in the network topology.
An operating system is an interface between the user of a computer and the computer hardware. The swap file system is used for memory paging in Linux operating system during the system hibernation. What term is used to describe a running program on Linux.
We highly recommend that you choose distributions which stay close to the stable upstream software releases. It relies on the crontab file. It is the default installation location of the.
The -e command option is used to display a human-readable version of the time of each message as well as its delta or the difference in time between subsequent messages. Imagine that there is no salt value applied before storing passwords in linux. It is used for fault tolerance repair system fun administration extensive storage configuration and more.
Requests for special processes or procedures in response to alerts will be considered as a modular service. Traditionally the mechanism of raising an interrupt of int 0x80 to kernel was used. This is a newer version of syslogd having several additional features.
Rsyslogd used to log system messages. JumpClouds Directory-as-a-Service Linux user management feature is a cloud-based directory services platform that manages user access to Linux servers regardless of location or type. The init system is also used to manage services and daemons for the server at any point while the system is running.
-1 option used in the above command tells which hashing algorithm to use 1 indicates md5 algorithm. Side note The -H command option is used to output time in a human-friendly format combining both -e and -L options and using a text pager. Salt value is a major component that strengthens the way a linux system stores password.
Other operating systems which also use the Linux kernel such as ChromeOS Android and Qubes OS are not discussed here. Having individual service accounts for each service serves two main purposes. It is not a good suit for the production system.
What will happen if there is no salt value at all. In RFCOMM channels 1-30 are available for use. The service command comes pre-installed with almost every Linux distribution out there.
Based on the information stored in the directory service server system authenticates whether the user is allowed to login or not. This page uses the term Linux to describe desktop GNULinux distributions. The fundamental purpose of an init system is to initialize the components that must be started after the Linux kernel is booted traditionally known as userland components.
Directory-as-a-Service and Linux Take Flight. Cron Background service that schedules tasks to occur at certain times. Using a simple command we are given a complete list of services.
Its the place used to place and install other software. Under which licensing model is Linux made available. While its main purpose is to start and stop scripts and create processes service can also be used to see what services are running or stopped at any given moment.
The short-term of the operating system is OS. On Linux as on many other Unixish systems name service is provided through a program called named. Requests to implement any special monitoring against applications or components that have been configured by the client or are run by the client will be considered as a modular service.
On Windows machines the service names port numbers and protocols can be found in the Cwindowssystem32driversetcservices file. These differences aside both protocol service multiplexers and channels serve the exact same purpose that ports do in TCPIP. The first and foremost reason why linux servers are way ahead than the Windows servers are there completely free and available as open source software.
It supports logging on local systems as well as on remote systems. Today the systentersysexit instructions. L2CAP unlike RFCOMM has a range of reserved port numbers 1-1023 that are not to be used for custom applications and protocols.
But most people like to mount hard drives under home misc. On Linux machines the etcservices file stores the information about the various services that client applications might use. By open source means you can easily see the code available that was used for creating the Linux Kernel and also modify the code to fix any bugs etc.
Daemons These are background services printing sound scheduling etc that either. It is a collection of software that manages computer hardware resources and offers common services for programs of the computer. Necessarily linked to Linux or Unix but was created by the community to combat the wide-spread use of hacker in this sense.
After trapping the interrupt kernel processes it and changes the execution mode from user to kernel mode. Its the place used to mount the shared directory of the NFS service.

Chapter 3 Choosing A Linux Distribution The Ultimate Linux Newbie Guide

Lfcs Managing System Startup Process And Services Sysvinit Systemd And Upstart Part 7

Why Is Hybrid Cloud Strategy A Must For Financial Services

Database Cluster For E Science
10 Linux Distributions And Their Targeted Users

How Linux Runlevels Affect Running Services Cloudsavvy It

Introduction To Azure App Service Part 2 Hosting Web Applications With Web Apps

Concise Linux An Introduction To Linux Use And Manualzz

Linux 101 Demystifying The World S Most Customizable Operating System

Pdf Mmale A Methodology For Malware Analysis In Linux Environments
Pdf An Sdr Mission Measuring Uhf Signal Propagation And Interference Between Small Satellites In Leo And Arctic Sensors

Pdf Current Use Of Linux In Spacecraft Flight Software

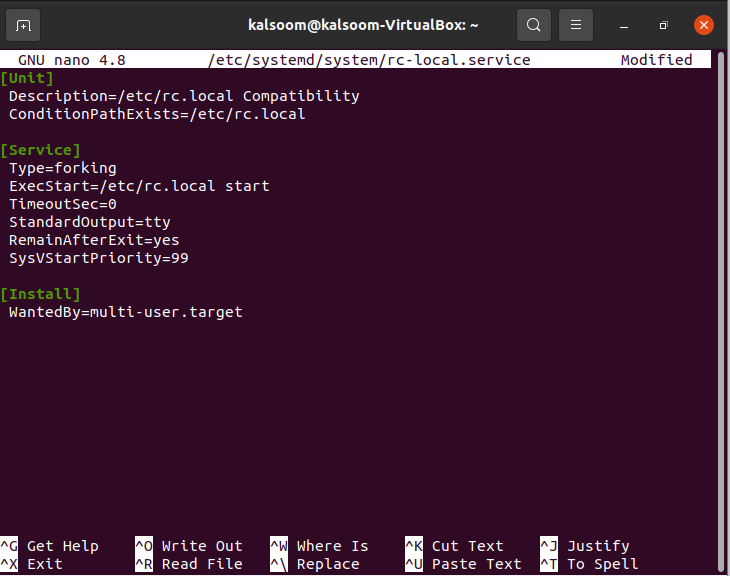
How To Create A Systemd Service Unit File In Linux Linux Shout



Comments
Post a Comment